Microsoft’s PhotoDNA: Leading the Fight Against Child Sexual Abuse Imagery
April 25, 2016
3 Minute Read
Courtney Gregoire works as a senior attorney in Microsoft’s Digital Crimes Unit, where she fights technology-facilitated crime against vulnerable populations including children and the elderly. Her blog post is part of Thorn’s hashing series, which highlights the benefits of hashing technology for industry, law enforcement, nonprofits, and service providers as they work to detect and remove child sexual abuse material online.
Microsoft’s Digital Crimes Unit is dedicated to helping fight the online exploitation of children. One persistent, horrendous crime is the distribution of child sex abuse imagery on the Internet. The children victimized in this material are first harmed when their abuse is perpetrated and recorded. They are further victimized each time that record is distributed. Last year, thanks to PhotoDNA, the technology industry was able to disrupt the distribution of over 4 million images, a 4-fold increase over 2014.
Every day, as many as 2 billion unique images are uploaded and shared on the Internet. Finding known child sex abuse images can be like trying to find a needle in a haystack. We needed an easier way to identify and detect these images, and that’s how the concept for PhotoDNA was born.
How PhotoDNA’s digital fingerprint finds the “worst of the worst” images of child abuse
In 2009, Microsoft partnered with Dartmouth college to develop the hash matching technology that develops a “PhotoDNA signature” for online photos that have been deemed the “worst of the worst” by the National Center for Missing and Exploited Children (NCMEC). This signature, or digital fingerprint, is created by converting the image into a grayscale format, creating a grid and assigning a number to each tiny square. Those numbers represent the “hash” of the image, a.k.a its “PhotoDNA signature.” This robust hash can then be used to find that photo wherever it has been distributed on the Internet, even if the photo has been altered.
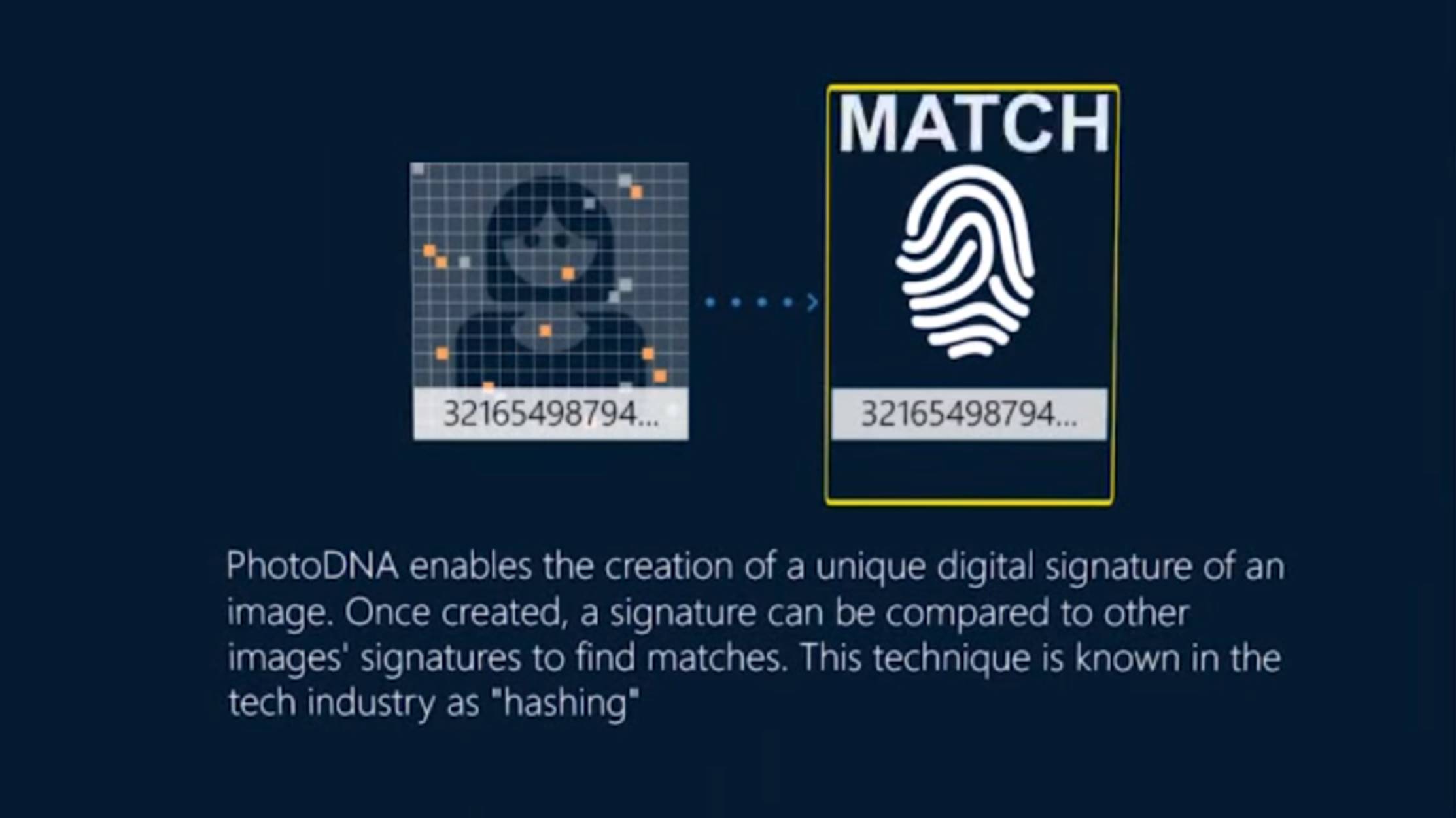
This process of identifying the image is fully automated. The program isn’t scanning for photos, instead it’s looking for the signature’s numerical match. Images are instantly converted to secure hashes and the hashes are not reversible so the signature can’t be used to replicate a photo. This allows companies all around the world to quickly compare millions of photos against a hash of known illegal content, while also respecting customer privacy.
A leading best practice for tech companies to combat child exploitation
PhotoDNA technology is completely free for qualified companies, organizations, and developers vetted through a third-party. We have shared it with more than 100 companies worldwide, including Facebook, Twitter, Kik, and Flipboard. Law enforcement agencies all around the world also use PhotoDNA to help with their investigations, including Project Vic, which is aiming “to create an ecosystem of information and data sharing between domestic and international law enforcement agencies.”
Microsoft’s PhotoDNA’s hashing and matching technology has become a leading best practice to combat child sexual abuse imagery on the Internet. We continue to strive to improve this technology as well. Since its formation in 2009, we have made some changes to make the technology quicker and easier to use. In December 2014, we added the PhotoDNA Cloud Service, which runs on Azure, and leverages the speed, security, and efficiency of the Microsoft cloud. In December 2015, we added Linux and OS X support and increased detection speeds up to 20 times faster.
There is a lot of work to be done here, and by working with the industry and sharing the PhotoDNA technology, we’re continuing the fight to help protect children.
To stay up-to-date on the latest developments, please follow the Microsoft Digital Crimes Unit on Facebook and Twitter.
Related Articles
Stay up to date
Want Thorn articles and news delivered directly to your inbox? Subscribe to our newsletter.


